Identity-First Security for True Zero Trust
You can’t execute a Zero Trust model without first trusting user identities, and that means authenticating them continuously–from the time they try to login to the moment they log out.
TruU and CrowdStrike have teamed up to add Zero Trust assessment (ZTA) scores to the TruIdentity Cloud authentication risk engine, providing the most comprehensive and efficacious Zero Trust solution with continuous identity at its core:
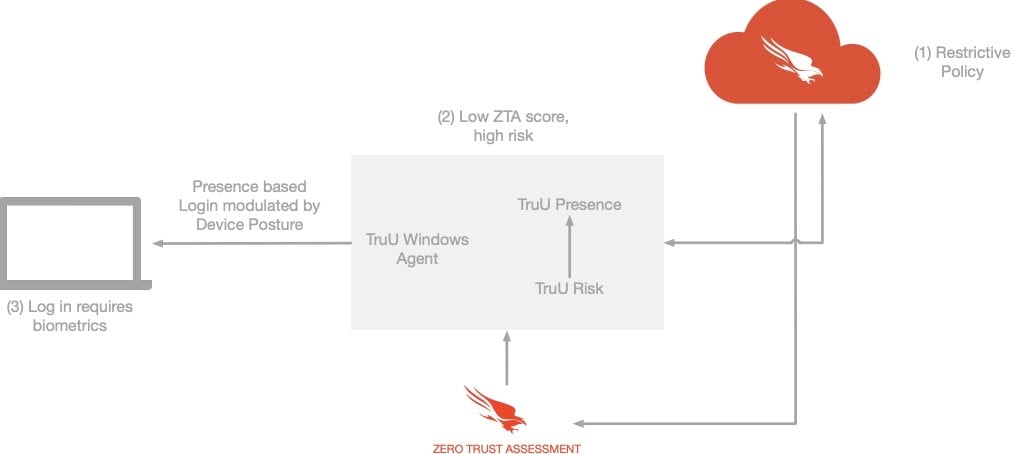
Simultaneous device risk data and identity authentication allow customers to implement policies that respond to potential threats as they happen by stepping up identity verification on compromised endpoints and limiting access to high-value assets associated with those endpoints.
No two users are the same, and TruU + CrowdStrike enables dynamic use policies to accommodate differences in behaviors, biometrics, environment, and more. Continuous identity coupled with device risk assessment allow for real-time threat response and foundational Zero Trust. Other benefits include:
- Keeping endpoint maintenance up-to-date through better authentication experiences
- Improving employee engagement by delivering seamless authentication for improved productivity
- Modulating identity authentication step-up with device trust levels to achieve optimal security
- Combining presence and dynamic environmental factors with other identity challenges to ensure utmost trust
- Removing productivity blockers from trusted devices
Step-up identity authentication on potentially compromised devices
TruU + CrowdStrike takes the endpoint ZTA rating and feeds it into the TruU risk engine for an overall risk score. The TruU risk score is compared against the user’s policy threshold, and if the score is within bounds, the user is logged in. If the score is higher than the threshold, then another factor is required for access.
Benefit
Ensures the combination of user identity and endpoint trust meets enterprise security requirements.
Stop authentication into high-value assets from compromised devices
Once authenticated into a potentially compromised device, TruU stops the user from further authenticating into servers or remote machines until the local device ZTA score is mitigated.
Benefit
Allows the user to authenticate at the endpoint while limiting the spread of data breaches.
Reward users with better experiences while keeping endpoints more secure
The authentication experience communicates and demonstrates more productive ways for users to authenticate when they follow prescribed endpoint update schedules.
Benefit
Boosts employee engagement across the enterprise so they care more deeply and keep their endpoints within acceptable security guidelines.
About TruU
TruU combines strong identity proofing, presence, biometrics, and behavioral markers in the continuous TruIdentity Cloud engine to deliver the most comprehensive passwordless solution for all physical and digital workflows. Its TruPresence capability is a groundbreaking innovation that allows individuals to authenticate into workstations, physical doors, and other sensing assets simply by being close to them and removes the zero-sum trade-off between better security and a better user experience.
TruIdentity Cloud comes with pre-built, standards-based integrations across the entire identity stack to support full-spectrum authentication. Remote onboarding and identity proofing, workstations, apps, servers, VPNs, Windows, Mac, and privileged access are all supported, as is physical access via badge readers. To discover how TruU can help you remove the largest security risk in your organization, visit https://truu.ai/.
About CrowdStrike
CrowdStrike® Inc. (Nasdaq: CRWD), a global cybersecurity leader, is redefining security for the cloud era with an endpoint protection platform built from the ground up to stop breaches. The CrowdStrike Falcon® platform’s single lightweight-agent architecture leverages cloud-scale artificial intelligence (AI) and offers real-time protection and visibility across the enterprise, preventing attacks on endpoints on or off the network. Powered by the proprietary CrowdStrike Threat Graph®, CrowdStrike Falcon correlates over two trillion endpoint-related events per week in real time from across the globe, fueling one of the world’s most advanced data platforms for security.
With CrowdStrike, customers benefit from better protection, better performance and immediate time-to-value delivered by the cloud-native Falcon platform. There’s only one thing to remember about CrowdStrike: We stop breaches.Learn more: https://www.crowdstrike.com/
© 2022 CrowdStrike, Inc. All rights reserved. CrowdStrike, the falcon logo, CrowdStrike Falcon and CrowdStrike Threat Graph are marks owned by CrowdStrike, Inc. and registered with the United States Patent and Trademark Office, and in other countries. CrowdStrike owns other trademarks and service marks, and may use the brands of third parties to identify their products and services.


